How Zero Trust Security Is Transforming RISE with SAP
Posted on December 11, 2025 by Laeeq Siddique

Introduction
With the increasingly rapid pace of changes in our digital world, security has never been more crucial. As companies increasingly shift their operations to the cloud, traditional models of security fall short. Introducing SAP Zero Trust Security, a new way for companies to protect their data and IT infrastructure.
Assumed compromise means you start from the position that all devices and users (called ‘endpoints’) both inside and outside your network are untrustworthy by default. As a result, this architecture changes the game when integrated with RISE with SAP. It enables SAP’s end-to-end offering to support the entire value-realization journey in a cloud-first world.
Therefore, RISE with SAP delivers an integrated solution that removes guesswork from business transformation. In addition, by harnessing the SAP Zero Trust Framework in this offer, SAP strengthens security for hybrid landscapes so that companies are more secure.
In this blog, we’ll talk about how SAP Zero Trust Security advances with RISE with SAP, why it’s important, and how it helps secure your SAP cloud services and hybrid landscape
Know about SAP Zero Trust Security in RISE
Redefining Security Models
Zero Trust Security is a network security model that treats everyone, inside and outside the organization, as untrusted by default. Unlike traditional security, which often places greater trust in users and devices within the perimeter, Zero Trust requires authenticating every user, device, and network before granting access to resources.
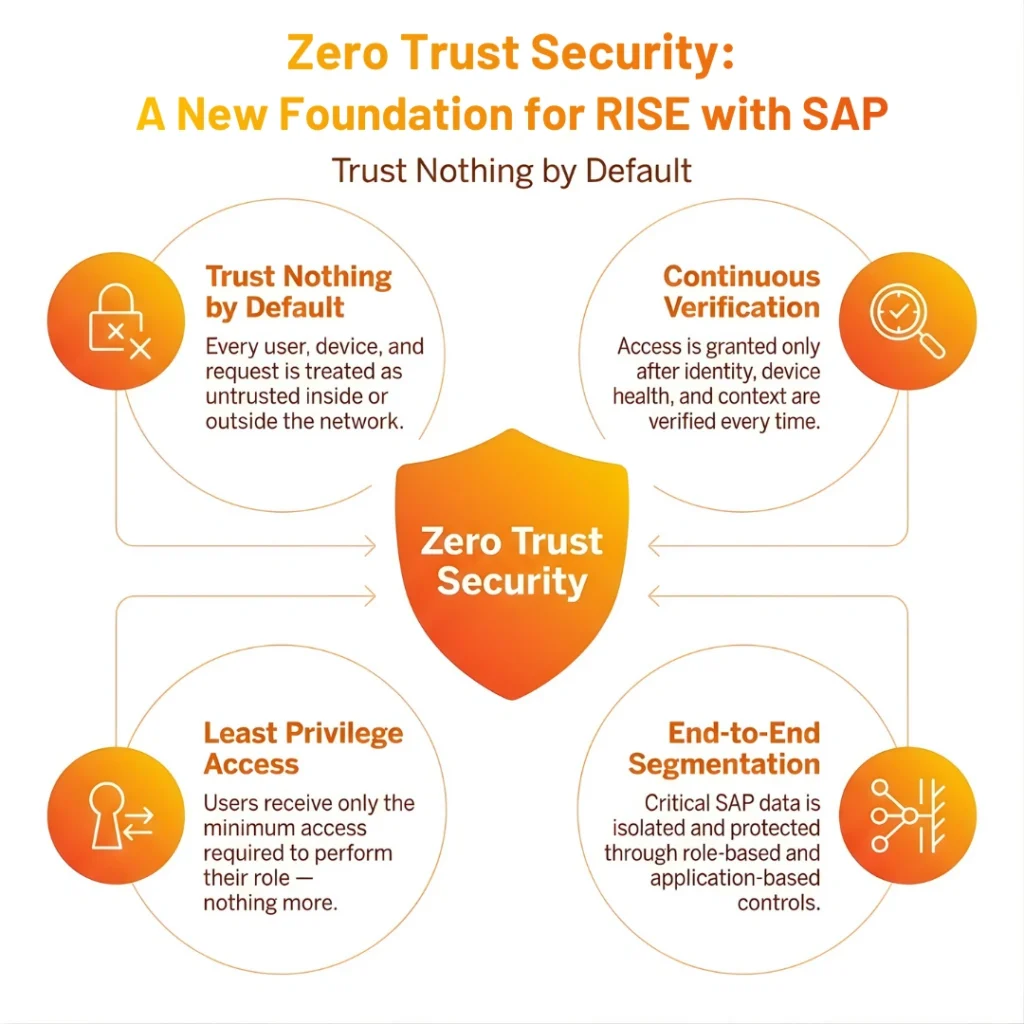
In SAP Zero Trust Framework this security concept provides particular added value because it also protects valuable business information within cloud settings and blocks unauthorized access at many places.
Key Principles of SAP Zero Trust Framework
Therefore, SAP Zero Trust Security is built on a few fundamental principles:
- Don’t Trust, Verify: Assume each access request comes from an untrusted network.
- Least Privilege User Access: Assume each access request comes from an untrusted network.
- End-to-End Segmentation: Segment exclusive data and restrict access based on the user’s role, device, or application
Benefits for RISE with SAP
There are several benefits when you incorporate ZTS into RISE with SAP:
- Stronger Locks Against Unauthorized Access: Zero Trust consistently verifies that everyone attempting to access the system has permission to do so and places strong restrictions on which users actually can, so bad actors have a very hard time getting in.
- Increased Compliance: Zero Trust model is now an added source of compliance with recent regulatory frameworks such as GDPR, HIPAA, and other data security requirements.
SAP Cloud Services: Secure and Dependable
Securing SAP Cloud through SAP Zero Trust Framework
Stability and Performance of SAP Cloud services. It is time to consider the addition of Zero Trust Security. And now here is a new way how organizations can continue securing while on board their SAP. Through Zero Trust, SAP is verifying every door into its cloud services
Advantages from Integrating SAP Cloud with Other Services
- Uniform security policies across cloud infrastructure: Zero Trust enables enterprises to preset consistent security rules on all layers of the SAP Cloud Infrastructure. By allowing enterprise administrators to manage access and security from a central location predictably.
- Advanced Threat Detection and Response: By adopting Zero Trust architecture, SAP enhances threat detection. It can automatically identify and respond to unauthorized access attempts or security exploits
Embedding Zero Trust into SAP Cloud services not only secures the environment but also gives businesses peace of mind that their data is always secure.
SAP Zero Trust Framework:
How to Secure Your Hybrid Cloud
Challenges in Hybrid Environments
As organizations transition to hybrid environments, protecting data across multiple locations becomes more complex. A hybrid environment involves data moving between on-premises systems and cloud services. This requires integrated security to ensure protection across both systems.
This is where you can see the value of Zero Trust in action, with features that:
- Consistent Security Policies:
So, users applying a Zero Trust methodology can guarantee that security policies remain consistent whether they are on-premises or in the cloud. - Simplified Access Controls:
For hybrid scenarios, fine-grained access to resources is maintained by dynamic verification. Only the systems to which users and devices are entitled may be accessed.
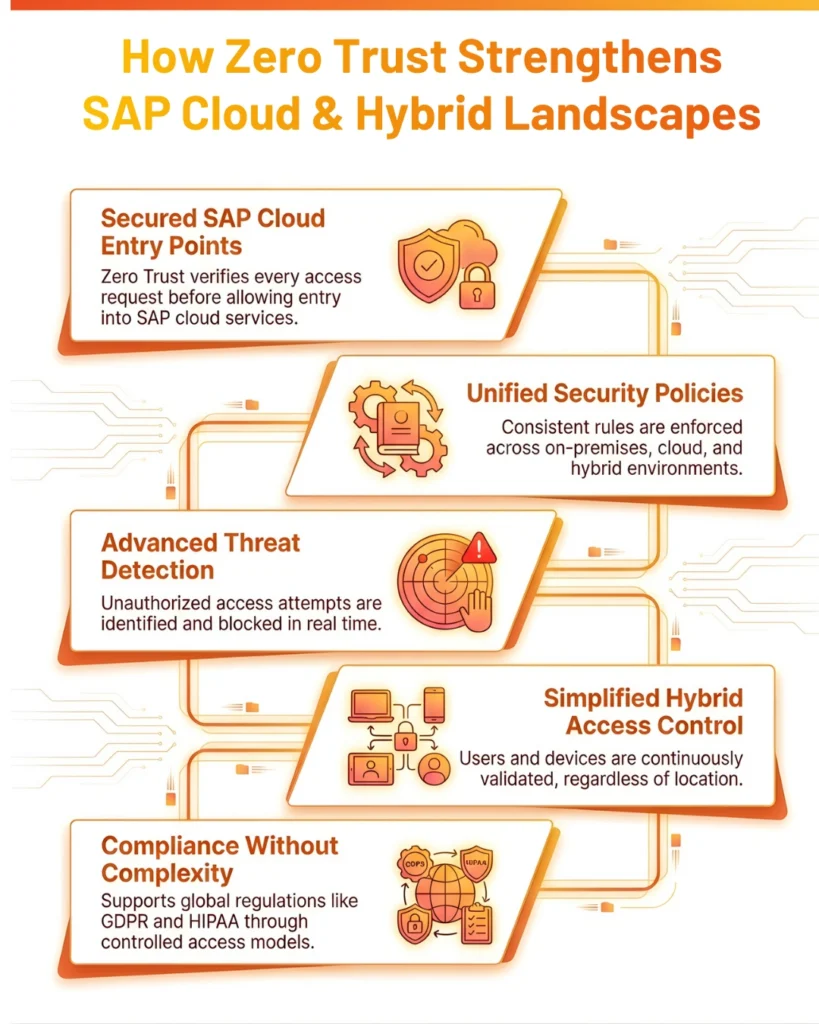
With Zero Trust, SAP customers can take comfort in knowing that the same level of protection is applied equally across their hybrid systems, regardless of location whether they are on-premises or in the cloud.
Competitors’ Analysis
No Trust in the SAP Community
The role of Zero Trust in the SAP realm is rising. Many blogs and success stories in the SAP community highlight how companies are using Zero Trust Security to protect their SAP cloud environment. Organizations that have adopted a Zero Trust strategy are seeing better operational effectiveness, reduced security risks, and improved risk management.
SAP’s competitors are also progressing with Zero Trust in their cloud services. However, moving cloud services is easier said than done, and customers face significant cost overheads,” says Subbu. Customers struggle to build a new data mesh after investing heavily in their backend processes. But SAP can lead the change thanks to its own investments.
Conclusion
SAP Zero Trust Security is now not just a buzzword it’s mandatory in the cyber age. By embedding Zero Trust into its cloud solutions, RISE with SAP enables businesses to further protect their data, secure their cloud, and seamlessly connect their on-premises and hybrid footprints.
Zero Trust in SAP Cloud Services marks a major advancement in cloud security. It helps companies respond strongly to escalating threats while meeting global requirements. Finally, Zero Trust companies can confidently start their digital transformation journey, knowing their data is protected at every level.
If you would like to roll out Zero Trust Architecture for your SAP infrastructure Cremencing Solutions will support you. We are SAP Custom Development experts and can add more value to your security model by Zero Trust approach.
For more insight read our Blog How to Automate Security Monitoring for RISE with SAP and SAP BTP
FAQs
What Is Zero Trust Architecture For SAP?
Zero Trust Architecture is a security concept where no resource, internal or external, is trusted by default. Users and devices are continuously authenticated. Only trusted users and devices can securely access resources, strengthening SAP security.
What does Zero Trust mean for RISE with SAP?
Zero Trust strengthens protection of SAP resources by verifying each access request, allowing only approved users and devices to access SAP resources. This also reduces the chance of unauthorized access and increases compliance with data protection regulations.
How can Zero Trust benefit cloud services?
Zero Trust enhances cloud security by enforcing uniform security policies, so better threat detection is provided, helping to guarantee only legitimate users can have access to sensitive cloud services. This results in higher reliability and security of your SAP cloud.
Why is Zero Trust necessary in a hybrid environment?
Zero Trust enables organizations to enforce strict and consistent security policies across on-premises and cloud environments. This means wherever data is, it is protected, and businesses can confidently manage their hybrid environments.
